Usenix Protection '24 Summer Accepted Papers Cryptographically safe code prescribing stringent adherence to the design and functioning of blockchains/distributed networks. This code can just be broadened or customized with approval from the network agreement mechanism. In generative expert system (AI), the procedure of offering Click here! guidelines to guide a version toward generating the preferred result.
Eu Taxonomy: Clarifying New Demands Due January 2024
When it involves medical AI, obtaining governing authorization to market an item within the EU is a long and difficult procedure. To understand the prevalence and attributes of such dark patterns, we initially research Apple's alert guidelines and identify four patterns that violate standards. We after that establish ATTCLS, an ATT sharp classification structure that integrates contrastive learning for language modeling with a completely linked neural network for multi-label sharp pattern classification. Finally, by applying ATTCLS to 4,000 iOS applications, we expose that 59% of the alerts make use of 4 dark patterns that either mislead individuals, incentivize tracking, consist of complicated terms, or leave out the objective of the ATT approval.- The 2nd column in the figure sums up the frameworks' summaries of the vital def ...From the challenges recognized, we make suggestions for increasing the adoption of passwordless authentication.Whether you're in India or anywhere else, understanding prompt design can considerably improve your communications with AI systems, making them extra effective and insightful.If utilized, it is generally the last file created prior to writing the resource code.
Get Yourself A Basic (Dexterous) Mentoring Certification
An essential concept in CMMI representing that work products resulting from projects and organizational processes need to be utilized and valuable to the work and allow performance. The job products need to be kept present to show how work is carried out or improved. Protection extensive improves safety by enhancing the initiative needed in an assault by placing numerous obstacles between an opponent and venture computing and info sources. A course of controls used in a database management system (DBMS) to make sure that deals are refined in an atomic, consistent, separated and long lasting way (ACID). This class of controls implies that only serial and recoverable schedules are permitted which fully commited transactions are not discarded when ruin aborted purchases. A coherent collection of efficiency steps organized into four categories that consist of typical financial measures and customer, interior company procedure and discovering and growth perspectives.Appendix B Kql Kinds
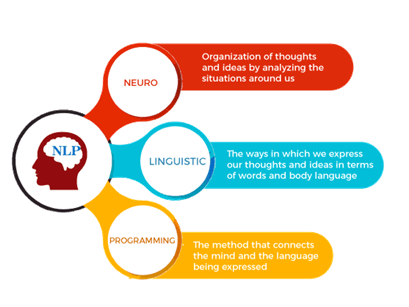
Incorporating "extremely" and "somewhat" familiar reactions, 77% had knowledge with monitored machine learning, 74% generative AI, and 73% NLP. In this instance, Darktrace's Autonomous Action capability was configured in Human Verification setting, suggesting any type of mitigative actions required hand-operated application by the customer's security team. Between May 7 and June 4, Darktrace recognized a wide variety of dubious exterior connectivity on one more customer's atmosphere. Darktrace's Hazard Study group further examined this activity and assessed it was likely indicative of WarmCookie exploitation on consumer devices. WarmCookie examples explored by external scientists were observed communicating communicated over HTTP to a hardcoded IP address making use of a mix of RC4 and Base64 to safeguard its network web traffic [1] Nonetheless, as privacy concerns mounted, Google has considerably restricted gadget identifier usage through Android system updates. In the new age, tracking SDKs are just allowed to utilize user-resettable identifiers which individuals can additionally opt out of, triggering SDKs to look for different approaches for reputable individual identification throughout applications. We create an evaluation pipeline for a considerable massive examination of this sensation, leveraging kernel-level instrumentation and UI screening techniques to automate the recording of application data operations at runtime. Using our pipe to 8,000 Android applications, we identified 17 third-party tracking SDKs that keep identifiers on external storage space. A company supplying services to one or more (interior or outside) customers. An activity that gives an assured exchange of worth between a service provider and customer, product or work item. Solutions do not always generate substantial or storable items; in such circumstances, the solution itself is the deliverable. Group of directly identifiable info (PII), either whose nature is delicate, such as those that associate with the PII principal's most intimate round, or that might have a substantial impact on the PII principal. Our evaluation of existing modern CPU fuzzers shows that they create programs that are either extremely simple or perform a tiny fraction of their instructions because of void control circulations. Integrated with expensive instruction-granular insect discovery devices, this brings about inefficient fuzzing projects. We provide Cascade, a brand-new approach for generating legitimate RISC-V programs of approximate length with extremely randomized and interdependent control and information flows. Waterfall counts on a brand-new technique called crooked ISA pre-simulation for ensnaring control moves with information moves when producing programs. This entanglement leads to non-termination when a program triggers a pest in the target CPU, making it possible for Waterfall to find a CPU bug at program granularity without introducing any kind of runtime expenses. Tasks carried out to gather info and appoint numerical values connected to the tasks, actions and outputs of following a process. This information is evaluated to establish the performance and efficiency of a procedure. A primitive is a fundamental interface, block of code or standard functionality that can be released and reused within more comprehensive systems or user interfaces.Is it tough to learn NLP?